“Your account is hacked” — a phrase that makes us think somebody is doomed this time. While we tend to get chills from the fact that it could have been our own account, imagine the situation of a company when their website is hacked. There are data, credentials and what not being regularly updated to store them there, as well as updates that inform their clients or general masses about their situations.
Recently, there had been cases where some banks in our country fell prey to a group of hackers and lost millions of dollars. This happened since the servers of the banks were linked to a system called SWIFT, or Society for Worldwide Interbank Communication, which is a global finance messaging system which is used by various organizations to transfer billions of dollars every day.
One of those organizations was the NIC Asia Bank. The hackers had used malware in their system which made it possible to make around 4.4 million dollars for them. As per dailymail.co.uk, the Deputy Governor of the Nepal Rastra Bank (NRB) stated that most of the stolen amount had been recovered, and the chief of Nepal Police’s Central Investigation Bureau stated that they were still working on getting the rest.
Then there are popular “hacktivists” (who claim that they are) that have tried to come in the limelight by doing stuff like claiming to breach into the Nepal Telecom server and gaining all the details including username, citizenship number and other available details. Apparently, a teenager under the alias “Anonymous #opnep” has even described it on a Facebook page. He managed to hack into 200 websites while just being a plus-two student (high school), as stated by The Himalayan Times.
Before moving any further, here are some common terminologies that are used in the hacking world, since there’s me who used to think using private browsing (incognito mode) would already make me a hacker and the word “hacking” would literally define each of its branches (I really hope I am not the only one, *sigh*):
- Ethical hacker (White hat): A hacker that tests the vulnerability and does assessments accordingly.
- Cracker (Black hat): A hacker who gains unauthorized access to systems for their gain.
- Grey hat: A hacker who is somewhere between ethical hacking and cracking, to identify weakness and reveal them to the system owner(s).
- Script kiddies: A non-skilled hacker who gains access to systems using pre-made tools.
- Hactivist: A hacker who uses hacking to send messages for purposes (like social, religious and/or political) by hijacking into a website and leaving a message.
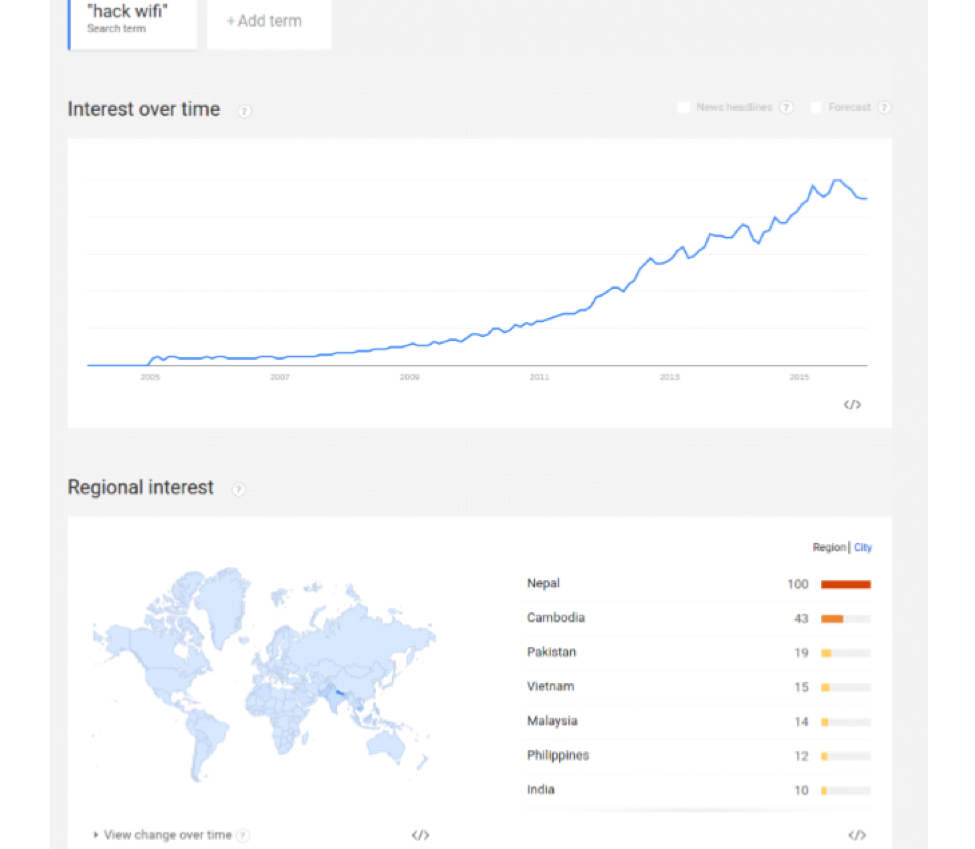
It may (or may not) be very surprising to know, but Nepal surpassed all the other countries on most googled terms related to hacking as stated by an article by The Social Media Today published in 2016, such as “how to hack” and “hack Wi-Fi”. Can’t deny the fact that I’m one of the contributing factors. Eek!
Also, a survey report by Rigo Technology reveals that out of 31 organizations who were asked the question what do you consider to be the greatest risk in your Organization?, the organizations that checked the ‘hackers’ option consisted of 51.60 percent, while the ones who checked the ‘malware’ option consisted of 58.10 percent.

While researching to obtain these details, recently we got a chance to have a conversation with Bijay Limbu Senihang, the Chief Technology Officer of Rigo Technology who has also been the IT Security Trainer at Laba Nepal and an independent IT security researcher. What follows is the edited transcript of the conversation:
TechLekh: What sort-of services do you provide on a regular basis and what are the types of clients that you encounter?
Mr. Limbu: As a part of Security Division, we provide cyber security services such as Penetration Testing, Information System Security Audit, Vulnerability Assessment, Cyber Incident Response, Cyber Security Consulting, IT Governance Consulting and Managed security services. We also provide Cyber Threat Monitoring Service, Cyber Security Operation Service. Most of our clients are Financial Organizations.
TechLekh: We have witnessed like 200 sites being hacked by a single person. What are your thoughts on the current security systems that the government as well as other organizations implement?
Mr. Limbu: Our organization is composed of different levels of security professionals whose main motive is to protect our client data and system. 200 websites being hacked by a single person seems to be big, but in my viewpoint, it is just the beginning. I have audited and tested more than 100 organizations and more than 200 system and application of Nepal, and the problem is big.
Let me start from the top. The first thing in the Top Level management of the Government is that they do not have a concrete idea regarding security. No policies, plans or procedures regarding cybersecurity are strong enough in the day.
We are transforming into a Digital age but are ignoring the fact that the digital system today needs extra security. If we talk about private organizations, the top level management must understand that security is not an IT issue, it is a business issue. Since IT has become the business enabler, we need to invest in the Information Security and Cyber Security. And if we move towards the bottom, everyone must know the importance of cyber hygiene.
TechLekh: The government has separated around 4.98 billion for the very purpose. Do you think that is enough?
Mr. Limbu: Separating fund is not enough unless you have valid objectives & goals with a proper plan, and you need a team of experts. Firstly, to secure our cyberspace, the Government must bring definitive plans for critical sectors such as Cyber Security for Government Agencies, Cyber Security for Telecom, Cyber Security for Financial Sectors and Cyber Security for ISPs.
TechLekh: What means is widely used to hack into websites here?
Mr. Limbu: If you talk about Nepali websites, the use of default credentials and SQL injection may be the most common methods.
Whatever the case may be, hacking is hacking, and hacking is a crime (in most scenarios viz. ethical hacking) despite being seemed “cool”. For the organizations and people whose identity is concerned, it is one of the worst nightmares.
As Mr. Limbu said, knowledge of cyber hygiene among lower-level staffs is a must, because at the end of the day, they deal with the transactions, and if they’re not made aware of it, then all is lost. In fact, it is the very reason why the SWIFT hack took place. It was because a malware got into the system and the staffs operating the system were not aware of it. If there’d been proper security mechanisms in place, then this should not have happened.
There had been a recent case in July 23, where the security of 50 government sites, including the Ministry of Defense was taken away by a group of hackers who wish to call themselves “Paradox Cyber Ghost”. They had broken into the sites for a “vulnerability test” as they stated. A more recent case of hacking in which popular online medias like OnlineKhabar, and Baahrakhari were used by hackers (or unauthorized personnels) to install scripts for cryptocurrency mining also took Nepali cyberspace by storm.
Maybe since there are very few certified ethical hackers in the country, we require much more of such resources to strengthen the security of the websites that we already have. Somebody locking something important on display in a fragile glass safe with only a strong lock makes no sense as far as security is concerned, does it? We will need to protect it, or maybe change the entire safe and replace it with a safe made up of a stronger material. That’s how it is supposed to be for now.
There’s this phrase in Nepali, najik ko tirtha hela, that translates to “The nearby shrines are ignored”. We fail to see the value of the resources that we have nearby. It’s high time to become aware of it and use our own resources rather than hiring or buying something from outside, because who else would know us better than ourselves?
Editor’s Recommendations
- Nepal Police to Establish Cyber Bureau
- Cyber Heist Hits NIC Asia Bank
- Nepal Television Official Website Gets Hacked
- Nepal’s Official .np ccTLD Registration Website Gets Hacked
View all latest articles on News. Stay updated!
-
ZTE Blade A55 with 90Hz Refresh Rate Launched in NepalHIGHLIGHTS The ZTE Blade A55 price in Nepal is Rs. 11,999 (4/64GB) and Rs. 12,999…
-
ZTE Blade A35e Launched in Nepal: Cheapest of the BunchHIGHLIGHTS The ZTE Blade A35e price in Nepal is Rs. 10,499 (2/64GB). The phone is…
-
2025 Ather 450S Arrives in Nepal: Improved Range at Affordable Price!HIGHLIGHTS Ather 450S price in Nepal is Rs. 3.25 Lakhs. The 2025 Ather 450S is…